apache benchでパーフォーマンス測定してみる。
$ ab -n 10000 -c 300 https://ras.viasv.com/wordpress/ This is ApacheBench, Version 2.3 <$Revision: 1826891 $> Copyright 1996 Adam Twiss, Zeus Technology Ltd, http://www.zeustech.net/ Licensed to The Apache Software Foundation, http://www.apache.org/ Benchmarking ras.viasv.com (be patient) socket: Too many open files (24)
ファイルを開きすぎ?
$ ab -n 10000 -c 30 https://ras.viasv.com/wordpress/
差がありすぎだけれど、raspi2ではこんなもんでしょう。
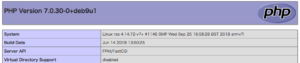
FPM/FastCGIを有効にしてabで再計測
| https://kusanagi.tokyo/about/ | ras.viasv.com | ||
| 測定方法 | ab -n 10000 -c 300 https://kusanagi.tokyo/ | ab -n 10000 -c 30 https://kusanagi.tokyo/ | ← |
| Server Software | nginx | Apache2 | Apache2-FPM/FastCGI |
| Server Hostname | kusanagi.tokyo | ras.viasv.com | ← |
| Server Port | 80 | 443 | ← |
| Document Path | / | /wordpress/ | ← |
| Ducument Length | 6952 bytes | 23213 bytes | 37504 bytes |
| Concurrency Level | 300 | 30 | 30 |
| Time taken for tests | 9.643 seconds | 1300.526 seconds | 1380.342 seconds |
| Complete Requests | 10000 | 10000 | 10000 |
| Failed requests | 0 | 0 | ← |
| Write errors | 0 | — | ← |
| Total transferred | 71680000 bytes | 234710000 bytes | 378350000 bytes |
| HTML transferred | 69520000 bytes | 232130000 bytes | 375040000 bytes |
| Requests per second | 1036.97 [#/sec](mean) | 7.60 [#/sec] (mean) | 7.24[#/sec](mean) |
| Time per request | 289.305[ms](mean) | 3901.578 [ms] (mean) | 4141.025[ms](mean) |
| Time per request | 0.964[ms](mean.across all concurent requests(*2) | 130.053 [ms] (mean, across all concurrent requests) | 138.034[ms](mean, across all concurrent requests) |
| Transfer rate | 7258.78[Kbytes/sec] recived | 176.24 [Kbytes/sec] received | 267.67[Kbytes/sec] received |